China fingered for Afghan Govt attacks

Chinese hackers have targeted nearly all major Afghanistan Government websites by hacking an official content delivery network (CDN) and gaining a foothold to attack western governments.
Hackers popped the network run by the Afghan Ministry of Communications and IT which delivered malware to many of the Government’s websites including the Australian embassy.
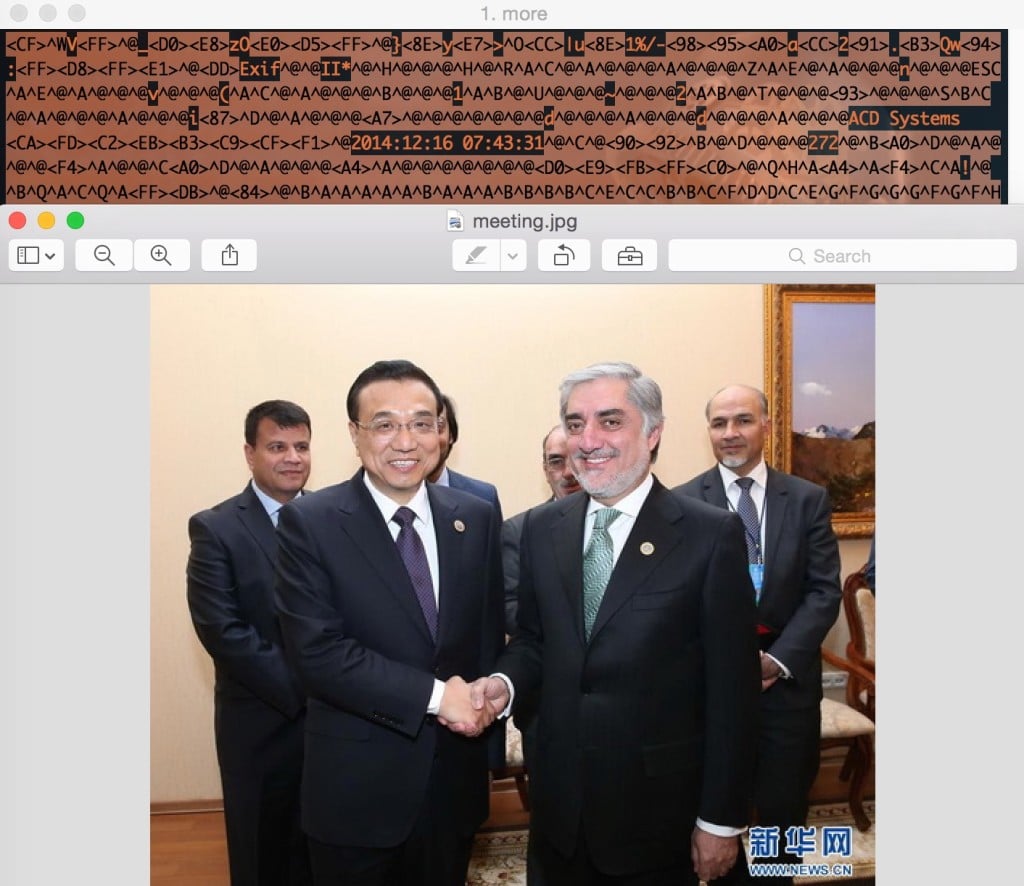
Afghanistan’s agencies for finance, education and justice were among the nine listed as falling victim to the attack, according to ThreatConnect researchers who found the watering hole attacks closely coincided with a meeting on infrastructure development and bilateral cooperation in Kazakstan between China’s Prime Minister Li Keqiang and Afghanistan’s government chief executive officer Abdullah Abdullah.
The researchers said an image used to serve the malware was modified only hours after it appeared to be taken at the meeting.
Such a hack would be of interest to China, researchers said, given that the country is building regional influence and might see an opportunity in the vacuum of the West’s military withdrawal from Afghanistan.
Beijing is also building transport infrastructure in the region and facilitating multilateral peace talks with the Taliban under its South Asian strategy.
“By exploiting and co-opting Afghan network infrastructure that is used by multiple ministerial level websites, Chinese intelligence services would be able to widely distribute malicious payloads to a variety of global targets using Afghanistan’s government websites as a topical and trusted distribution platform, exploiting a single hidden entry point,” the threat intelligence team (TSIRT) wrote in an advisory.
“This being a variant of a typical watering-hole attack, the attackers will most likely infect victims outside the Afghan government who happened to be browsing any one of the CDN client systems, specifically, partner states involved in the planned troop reduction.”
Naming conventions used in the Afghanistan attack dubbed Operation Helmand were similar to those in East Asia hacking operations.
The attack also bore similarities to a June watering hole attack in which a malicious Java file was served on the website of the Greece embassy in Beijing during a diplomatic meeting to Athens.
The team warned enterprises to monitor content delivery networks and ensure server response headers were configured to push third party content from narrow white lists.